-
Posts
2836 -
Joined
-
Last visited
Content Type
Profiles
Forums
Store
Downloads
Recruiting - 2020
2019-2020 Football Season
Football
Entertainment
Sports
News and Business
Cloak Room
Transfer Portal
Recruiting
Events
Posts posted by TXSG8R
-
-
- Popular Post
- Popular Post
Just to remind people the power of all the phone recording and social media. This is how the cops originally framed the incident.

Without those people distracting those poor cops and recording stuff, George is just another dead black guy.
-
 2
2
-
 3
3
-
 9
9
-
 3
3
-
4 minutes ago, WhatTheBuck said:
I’ll bet the Fox News ratings are plummeting again.
Paragons of empathy.
-
1 hour ago, Nice Guy Eddie said:
My Houston neighborhood has been gentrifying for a 2 decades now. Harris County has struggled to clearly differentiate between original homes from the 40s, original homes that have undergone major remodels and new homes that dwarf the originals. I'm in a home that was remodeled 25 years ago and Harris County attempted to value my home as a new one. I've had to argue (successfully) that my house is no where near a new home. My point is that your neighbor doesn't sound like a comparison to your house.
Both of your land values should be similar as I believe many jurisdictions, if not all, used a formula to calc land value for a given subdivision/section.
Oh I agree it’s not apples to apples, but I also don’t think the delta should be $200k either just because my house is newer (9 years old at this point).the shitty part is it’s incredibly hard to find comps for my house because Killeen is almost entirely cheap homes, so it’s really difficult to ever find anything accurate. We did have an appraisal done a little over a year ago for a refinance, and we were able to knock back the last attempt at raising us. I’ll try to use that again because I doubt the appraisal would be that far off in 15 months or whatever it’s been.
-
House value went from $380k to $495, land only went up $5k. The house directly across the street sold for $350kish less than 6 months ago. Granted, that house is 50 years older than mine, but it’s sitting on about the same acreage and has a pool and all kinds of extra improvements I don’t. This is in Killeen FFS.
-
3 hours ago, Nice Guy Eddie said:
Isn't Gaetz from the panhandle? Wouldn't Trump and Co from Palm Beach not think the best of panhandle Floridians? That's practically Alabama.
The most racist people I met at UF were from the Hollywood/So Fla area.
-
Yea, that coverage area will be 2.4Ghz, not 5. It will also be the bleeding edge of usable signal, marketing gonna market. Just like the advertised speed will be 1 device like a foot away from the wired AP. None of their shit reflects real world usage. Wireless mesh is great if you don’t have the option to wire your backhaul, but it’s always going to suffer from physics. I haven’t messed with orbi before, we tend to push TPlink Deco, but usually you can add some more APs to increase your coverage if you still have some weak spots.
-
Don't get a stronger router. Get a mesh/distributed system, preferably with a wired backhaul between the APs and gateway (or primary and extenders). You want as much stuff on the 5Ghz spectrum (more/protected channels so you can reduce/eliminate, faster speeds since the 2.4Ghz spectrum maxes out at 150Mbps), which doesn't propagate as well through obstacles or carry as far. You're better off having multiple access points that are closer to each device. The general rule of thumb is one wall away.
-
 1
1
-
-
With gaming he will likely run into issues due to being double NAT anyway. Everything on your side of the modem is a private subnet. When you hook his router up he is going to get a private subnet hooked to a private subnet, which furks up return traffic.
Why would the network connection upstairs go to the wan side of your router? That should be the modem. All your house ports should go to a switch/LAN side of your router.
-
3 minutes ago, Machinator said:
You guys don't like Mike White very much, right?
Yea, most gator fans hate him. Pretty good recruiter, lots of the same mistakes year after year. If Nembhard didn’t transfer to Gonzaga and Key doesn’t almost die on the court, we probably could have gone pretty deep just on talent.
-
I can’t remember being this frustrated watching a game. The FT disparity is fucking ridiculous, especially with how much we have been driving it and playing under the basket.
-
Well that’s about as shitty a draw as you can get for Bayern. We are getting two final worthy teams in the quarters and semis. If they can pull this off again, Flick needs to get a statue made.
-
22 hours ago, MonkeyDoughnut said:
Just know you likely will never have both on at same time, but if space works a good "mantle mount" takes care of the viewing height issue. I would prefer a different space so dont have to constantly raise and lower, but it's doable.
We have installed a couple of these on patios with fireplaces. They do work great at bringing the TV to a more comfortable viewing height, but it’s not something I would want to do on a TV I watch day to day. Move the FP, install a lower FP and mantle, or move the TV.
-
A TV without a tuner is a monitor. Category wire replaced phone wire, and doorbell wire, and most other low voltage wires out of convenience, not cost. It’s easier to carry a box of cat around for all those things instead of stocking and hauling different stuff. I agree coax will eventually go out, but not anytime soon. You can get over a Gb over the medium still, which is as fast as short 5e or long 6.
You aren’t streaming 40 4K movies over wifi concurrently, not uncompressed. HDMI 2.0b pushes 10Gbps, and that caps out at 4k60 4:2:0. Again, you can’t just look at advertised speeds and divide by the number of devices. The only place you’ll get that bandwidth is having a single device a foot away from the antenna in a test chamber that eliminates any other sources of interference. Distributed APs with wired backhauls are great (the same mentality should be applied to wired backhauls for all devices where it’s possible), but the money you’ll spend there to get pristine 5Ghz in every room will be orders of magnitude higher than running $7 of coax to every TV drop. Ideally you would run a coax, multiple category cables, and conduit to every drop to future proof the runs and make it user friendly to the next owner. It’s safer to cover all the bases IMO.-
 2
2
-
-
On 3/9/2021 at 9:01 AM, MonkeyDoughnut said:
One plus I really like is being able to place a TV anywhere without worry of "do I have a cable jack nearby". Inside, outside, garage... no worries... wifi is all I need. If I build a new house I wouldn't run coax anywhere and would limit ethernet to only the locations I planned to put wifi points. This plus being able to watch anywhere via mobile / casting / etc. can take with me to friends or hotel and such (depending on any service restrictions). Combine with being able to start and stop without speaking to anyone or having to wait for anyone entering my house ever.
This is a horrible take. Coax is worth running just for OTA even if you don’t want to use cable or satellite TV. I know you can push OTA through things like Tablo, but that device compresses your stream and requires your internet to be running to use it. You’d probably have to give up some money to a smart agent when you go to sell your house if you didn’t wire coax. Coax is some of the cheapest LV cable per foot to run, you aren’t saving much by skipping it
Wifi is a half duplex medium, so every device using wifi at the same time cuts your usable bandwidth. 4 devices means you’re only getting a quarter of the advertised speed (this is a simplistic example, the actual math is a little more complicated), which is normally impossible to achieve in a normal home anyway. Distance to your antenna, number of antennas, physical barriers, reflections, interference, all reduce your actual speed. The 5Ghz spectrum is the faster of the two, but it’s also the most susceptible to loss due to walls and physical distance. You want everything possible to be on a wired connection and save your wifi for mobile devices only.
-
 2
2
-
-
The one time I got selected for voir dire in regular JD I tried to go with the extreme burn this motherfucker answers to the prosecutors questions expecting the defense to strike me. It was an assault case, husband beat up his wife, forget the other charges. I wound up getting seated as a juror. I guess Im too stupid to get out of it.
-
 1
1
-
 1
1
-
-
Back to the OP, this article is great. Also supports Handcruser's stance on certs. They can open doors, but they aren't going to get you much in the way of usable experience for the job, especially if you just run through a bootcamp and shotgun test answers into your brain.
https://krebsonsecurity.com/2020/07/thinking-of-a-cybersecurity-career-read-this/
QuoteRarely am I asked which practical skills they should seek to make themselves more appealing candidates for a future job. And while I always preface any response with the caveat that I don’t hold any computer-related certifications or degrees myself, I do speak with C-level executives in cybersecurity and recruiters on a regular basis and frequently ask them for their impressions of today’s cybersecurity job candidates.
A common theme in these C-level executive responses is that a great many candidates simply lack hands-on experience with the more practical concerns of operating, maintaining and defending the information systems which drive their businesses.
Granted, most people who have just graduated with a degree lack practical experience. But happily, a somewhat unique aspect of cybersecurity is that one can gain a fair degree of mastery of hands-on skills and foundational knowledge through self-directed study and old fashioned trial-and-error.
One key piece of advice I nearly always include in my response to readers involves learning the core components of how computers and other devices communicate with one another. I say this because a mastery of networking is a fundamental skill that so many other areas of learning build upon. Trying to get a job in security without a deep understanding of how data packets work is a bit like trying to become a chemical engineer without first mastering the periodic table of elements.
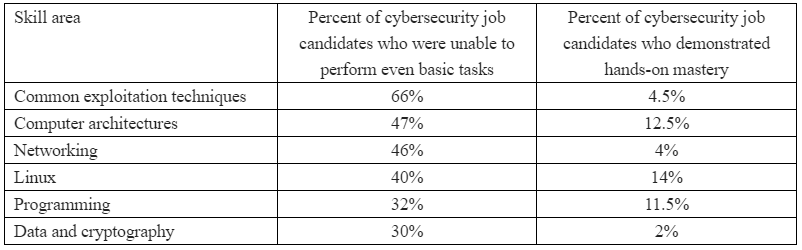
QuoteBut please don’t take my word for it. The SANS Institute, a Bethesda, Md. based security research and training firm, recently conducted a survey of more than 500 cybersecurity practitioners at 284 different companies in an effort to suss out which skills they find most useful in job candidates, and which are most frequently lacking.
The survey asked respondents to rank various skills from “critical” to “not needed.” Fully 85 percent ranked networking as a critical or “very important” skill, followed by a mastery of the Linux operating system (77 percent), Windows (73 percent), common exploitation techniques (73 percent), computer architectures and virtualization (67 percent) and data and cryptography (58 percent). Perhaps surprisingly, only 39 percent ranked programming as a critical or very important skill (I’ll come back to this in a moment).
How did the cybersecurity practitioners surveyed grade their pool of potential job candidates on these critical and very important skills? The results may be eye-opening:
 Quote
QuoteThe truth is, some of the smartest, most insightful and talented computer security professionals I know today don’t have any computer-related certifications under their belts. In fact, many of them never even went to college or completed a university-level degree program.
Rather, they got into security because they were passionately and intensely curious about the subject, and that curiosity led them to learn as much as they could — mainly by reading, doing, and making mistakes (lots of them).
I mention this not to dissuade readers from pursuing degrees or certifications in the field (which may be a basic requirement for many corporate HR departments) but to emphasize that these should not be viewed as some kind of golden ticket to a rewarding, stable and relatively high-paying career.
-
 1
1
-
-
3 minutes ago, Dbeasy said:
This thread is not about the best way to cybersecure networks, or your misguided viewpoint of the value of cybersecurity software. This thread is about a poor soul who wants a job in the cybersecurity industry. Your dismissal of a multi-hundred billion dollar industry that provides clear value to companies around the world is a viewpoint that makes no sense whatsover. Seriously. No sense at all. You would do well to quit while you are behind before digging yourself into a deeper hole. And for the OP, there are tremendous opportunities in cybersecurity software if you are interested. I should know. I've run a cybersecurity software company for the past few years.
And as to your viewpoint that human error is a big issue, but cybersecurity software has no value, there are thousands of products out there, including my company's, that monitor and alert for human errors made, providing a great tool for companies to quickly identify cyber vulnerabilities created via human error. Some of the biggest government agencies in the country use it for that purpose, as to commerical enterprises. So seriously, stop providing bad advice to this guy.
Quotelike I said, there are certainly tools that are useful in support of CyberSec
QuoteI'm not dismissing that there are usable CyberSec tools out there, I just don't see how going into sales would give someone a leg up on a guy that's jumping in as an analyst doing real CyberSec work out of the gate
QuoteI agree that there are software tools and approaches that are helpful, but that is such a limited scope in the CyberSec field.
Not sure if you are struggling with bias about security software or reading comprehension, so Ill highlight some of my quotes for you. I have never said software has no value in CyberSec. To the larger point, OP asked about work in the Cyber Security field, not Cyber Security software. His friend is hiring Cyber Security Analysts, not software developers. I think his lack of knowledge and experience led him to asking questions about coding, because a lot of people assume that IT work somehow involves code. He asked about certs like Sec+ and CISSP specifically. I'm not dismissive of software, but if he wants to work CyberSec as a career, IMO, he is going to be limited by going into sales for a specific software product and then jumping into full fledged CyberSec work for an organization. That was the route that DC threw out there with admittedly zero experience on the CyberSec side of the house. That's what you somehow jumped on instead of all of the other discussion.
And nothing you just said counters what I said about a lot of CyberSec software. Your software monitors and alerts for errors in a production environment? Congrats, your software is a canary. Its still helpful, alerts are always great, but you're now in post-incident mode regardless. Cyber Security, as a career path in a non-CyberSec software company, uses software as a tool, its not a panacea. Go back and read some of my first responses. None of it was intended to shit on software, it was offering the full scope of CyberSec as a career outside of software, because OP has no software experience and his buddy is hiring analysts.
-
That is the struggle, ease of use/efficiency versus security. DoD makes things easier on the security side by always defaulting to the security side of the argument, even at the expense of production. My guess is the private sector does the exact opposite.
MFA is better than simple PW. Biometric/physical multi factor is better than text/email just because of the ease of exploitation there. Yubikey is probably the best solution out there for MFA. The answer to your question is always money.
SSO isn’t inherently bad. Ideally each service would have unique authentication, but that’s stretching the limit for most users that struggle with one complex password change every 90 days. SSO should always be coupled with MFA. My guess is most of those third party sites offer a plug in to whatever SSO you’re using. You are correct though, by going that route you are giving attackers more surface area to work with, which is never a good thing.
One thing that should always be separated is OWA/mail services from the rest of your SSO stuff. Those should require unique authentication because of the amount of info/linkage of user data and MFA via email. Most attackers want to exploit email first because that puts them in the drivers seat for getting into everything else. Once I have your email account, I can just request a password reset on everything else and where does that usually go?
Edit: if you’re using a password for your email, work or personal, that is shared with anything else you’re definitely doing it wrong. Companies get breached all the time, and you don’t want that password you used for Etsy to wind up being how some script kiddie drains your bank account.The other thing that’s extremely critical is the separation of duties and privileges. How many orgs have that one IT guy that fixes everything? How many execs have permissions to view things that aren’t part of their workload? Network sec, host sec, audit teams, backups, etc should all have very explicit divisions in their permissions to avoid an exploit of one guy giving an attacker all the keys. For a small org with literally a one man IT staff, he should still be separating those duties with unique authentication to reduce surface area. Yes, it’s more of a pain day to day, but it also reduces the pain of a breach. Your mentality for security should always be when, not if, you’ll get breached. You make them earn every inch.
-
 1
1
-
-
I replied before coffee. In case it wasn’t clear, first paragraph was in response to Dbeasy, the rest is for DC.
I should also add, that IT in general is rarely the issue in CyberSec in most well run organizations. A password breach isn’t usually an IT issue, it’s poor policy (PW complexity is too weak, change cycle is too infrequent, etc). Most orgs have been locking down firewalls and ports for a long time, it’s rarely an IT configuration issue that gets breached, it’s software zero day exploits in the software external to the org running it. Going back to Solarwinds, the orgs that were running it probably followed all the proper guidance on hardening. The problem wasn’t their IT security. It was a supply chain issue that injected a back door into all their hard work. This is why more software is rarely the right answer. Everything you add to your network is something else to be scrutinized, another product’s supply chain and internal security posture that you have to sweat. The more popular the software, the bigger the surface area a bad actor gains by exploiting.
-
On 3/6/2021 at 7:50 PM, Dbeasy said:
I must have missed some part of the conversation. I thought he wanted to go into the "cybersecurity" industry and I didn't think he was interested in just cyber processes. If that's the case, then working for a cybersecurity software firm may not be the right path forward. But if he wants to get out of Oil and Gas and wants to do something in cybersecurity, then there is a $248 BILLION dollar market he can be employed in that helps cybersecure organizations, commercial and government.
22 hours ago, DonkeyCigars said:You didn’t miss anything. Typical engineer with a narrow focus and in a siloed work stream who loses the forest for the trees. It’s why these guys rarely rise to C-Suite and it’s why CEO’s are rarely former CIO’s.
😛
Any orgs handling CyberSec strictly as a software or network issue and ignoring everything else are the ones that get fucked on the regular. Most events happen because of shitty passwords, lost data to phishing, social engineering, physical access, etc. I agree that there are software tools and approaches that are helpful, but that is such a limited scope in the CyberSec field. I'm sure companies are spending a mint on stuff, but that 248 billion dollar market isn't riding on the backs of button pushers for that software. Its CTO/CIOs throwing money at a solution because everyone is super serious about Cybersec all of a sudden. If he wants to work in CyberSec beyond a lower tier IT role, the quicker he moves beyond a software suite and into more of the bigger picture the better.
Shitty C-suite execs like to throw buzzwords around or throw money at a software solution without understanding the depth they are in. Holistic approach is the opposite of a narrow focus chief. Its also why RMF puts a lot more guard rails in place specifically on management, because those are the guys that usually fuck up an orgs posture the worst, purely due to the lack of personal convenience. A lot of CyberSec software solutions are canaries. They tell you after a problem occurs, which means you've already been compromised. The point of CyberSec is to be ahead of those kinds of issues. You don't want to lose the Gibson because Karen from HR uses the same password everywhere and because CEO DonkeyCigars decided to relax the policy on PW complexity and change cycle because it was totally a hassle. That's what happens way more often than some movie script foreign hackers breaching your network.
You admitted early on that you didn't know shit about CyberSec. Your last hot take kind of proves it. If your organization is handling CyberSec purely as an IT issue they are doing it wrong.
-
 1
1
-
-
9 hours ago, Dbeasy said:
I think you might be looking at the process of Cybersecurity. He’s talking about Cybersecurity software, and there are 2,000 firms out there. He probably could get a sales role if he can use his network to get in somewhere. They will train him on the products. If he can take a few Cybersecurity classes that will show the hiring company he’s serious about the transition. I would have hired someone like that.
I was CyberSec management for our program, but also the lead network engineer on our technical implementation of controls on both hosts and network. My experience is skewed by it being all DoD work, but outside of AV and a DoD specific host-based software that distributed and enforced patches and policies, we didn't use anything else on the technical side to secure anything. We used STIGs and SCGs to harden everything manually, only allowed the necessary ports, protocols, and services, yada yada. I don't see software solutions that can do that kind of work for you because its so specific and unique to every organization.
We also used a DoD specific scanning tool suite, so I could see a private side equivalent being something that sells well. That box is external to our network though, its not something thats just plug and forget. I just don't see many software options that would solve an issue without causing other vulnerabilities. Everything you add to a box or network is another potential vector for attack. I'm not dismissing that there are usable CyberSec tools out there, I just don't see how going into sales would give someone a leg up on a guy that's jumping in as an analyst doing real CyberSec work out of the gate. You may make less money, but I want the guy earning real experience, not someone that can regurgitate slick sheets from memory but not know how to use the tool outside of a carefully rehearsed demo.
-
I got it for the DC in Waco. You have to call every week to see if you need to come in. Like week 4 I got the report message. Drove up to Waco, found out it was some kind of error. We all got credit for jury duty without actually doing anything. I think they were just fishing for people that didn't check weekly/answer the summons, maybe that's what they do when they don't have any cases? I can only provide these answers.
2. I don't remember the amount, but it wasn't anything approaching 3 figures. Cooter may be right.
4. You cant even bring your phone into the building.
5. You have to wear a coat and tie. If you don't, they provide you with one that has probably been worn by 100 people that cant afford a coat.
-
 1
1
-
 1
1
-
-
6 hours ago, DonkeyCigars said:
Really? Maybe the term as I’m thinking about it is overly broad, but seems like “cyber security” is a very crowded space. I’m thinking of all the software that gets sold under that heading and the subverticals that Gartner cares about: application security, IAM, DevOps security, micro services and APIM security, Security as a Service, Network detection and response, etc.
Seems there are probably a hundred narrowly focused software companies trying to tackle specific use cases and problems and a dozen large platforms like IBM or something who are trying to sell the full solution?
There isn’t any kind of turnkey, out of the box solution for CyberSec. Proper CyberSec encompasses all parts of an organization and its subs, vendors, supply chain, etc. that’s why it’s hard. Solarwinds is a great example. Lots of companies bought an admin tool that opened a huge hole in their posture. Buying software doesn’t fix physical access, or insider threats, etc. like I said, there are certainly tools that are useful in support of CyberSec, but if companies are advertising a full solution they are selling fool’s gold.
-
 1
1
-
 1
1
-
-
10 hours ago, DonkeyCigars said:
Easiest way is to get a sales job selling cyber security. Before you neg me for insulting you, hear me out.
You will have to be trained and learn from the inside out, bottom-up, and then maybe you can work at nights/weekends to add depth and breadth to your technical skillset. The benefit of this route is trifold: 1) you probably won't lose as much earnings on your W2-- sales people, even bad ones, generally make much more than a basic/entry level analyst 2) you can look to internally transfer/upskill from a non-technical sales job to a technical role a lot easier and 3) you get a lot of at-bats and hopefully hear from a lot of different customers and CISO's what are the real problems keeping orgs up at night, you learn a talk track and learn how to speak the language so when you interview, you can fake like you know what you are talking about and be more convincing than some O&G guy taking some stabs in the dark.
Disclaimer: I am not in the cyber security space, I don't know much about the space, and I didn't stay at a Holiday Inn last night.
What would you sell in the CyberSec field? There aren’t a lot of tools out there that do much of the heavy lifting. Some scanning and audit tools maybe, but I doubt the sales side would get you any usable experience on the operational side. I don’t see many ways around starting at an entry position and taking your lumps working up the ladder.



Bleach Blonde Bad Built Butch Body in Congress? Oh you mean Marjorie!
in Cloak Room
Posted
He needed an evangelical beard in 2016 to give him some credibility with the Christian right. That’s why he picked Pence. In theory he’s beyond that since the evangelicals have rationalized all his past actions so now he will pick someone to bridge the next gap in his numbers. A woman makes sense, but I doubt it’s MTG. Stefanik is the safe bet, dark horse would be Nancy Mace from SC.